Dust attacks have become a popular way of malicious activity for hackers trying to break blockchain privacy. Dusting was used at first by programmers performing stress tests on a network and email blasts, but scammers are now using it to unmask address anonymity.
What is a Dusting Attack?
Crypto dust is referred to a very small amount of a certain coin or token, which could accumulate in a wallet for example as a result of airdrops or rounding of transactions.
Users sometimes don’t notice crypto dust because it tends to have very little fiat value. Certain wallets and exchanges even have functions to hide small balances. For example, the smallest unit into which a Bitcoin (BTC) can be subdivided is 0.00000001 BTC (by design). Usually referred to as 1 satoshi, it is currently worth around $0.0005 AUD – in other words, it would take about 20 satoshis for 1 cent AUD.
Dusting basically means sending a tiny amount of cryptos to various wallet addresses in an attempt to deanonymise them. By linking together the addresses of a given crypto asset, the hackers then track down the transactional activity of the corresponding wallets, analysing every address while looking for clues to identify the person or company behind each wallet.
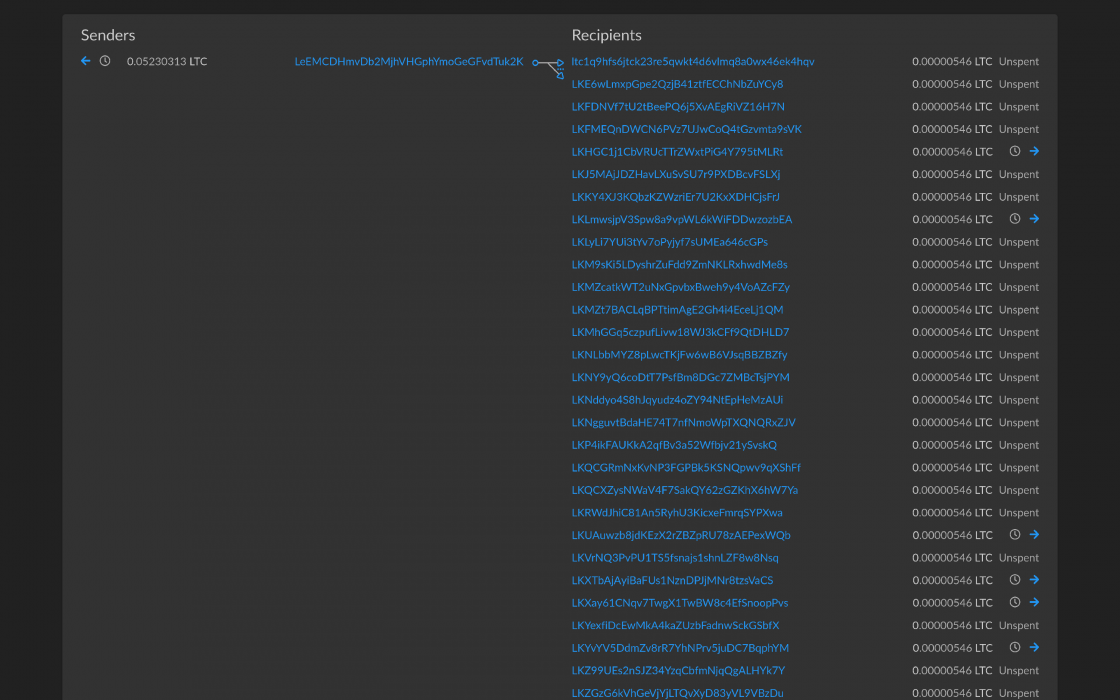
This manuver does not give the attacker access to your funds, as if you were under attack instead. Dusting could only allow guessing the identity behind those addresses.
Scammers and criminals are not the only ones to perform these kinds of activities, though. Law enforcement agencies could use this technique to bind an individual or even criminal organizations to an address, for example to target money launderers, contraband, or any large criminal network.
Dusting Attacks on the Rise
A reason why these malicious attacks are becoming so popular for hackers is that traders and large holders don’t seem to pay much attention to the small amount of tokens showing up in their wallet addresses.
Dust attacks were first seen on the Bitcoin network but are quickly expanding to Litecoin, BNB (Binance Coin) and other cryptocurrencies. A popular example of a dust attack occurred in late October 2018, when Samourai Wallet developers warned some users were under dusting attacks.
How to Protect Yourself Against Dusting?
First, get an export of your addresses and review the balances in each one. Check your addresses on a block explorer like Etherscan.io or Blockchair.com to see if you’re under attack.
To spot one, a dust transaction typically has one address on the sender side and hundreds or thousands of addresses on the other with the same small traces ent to them.
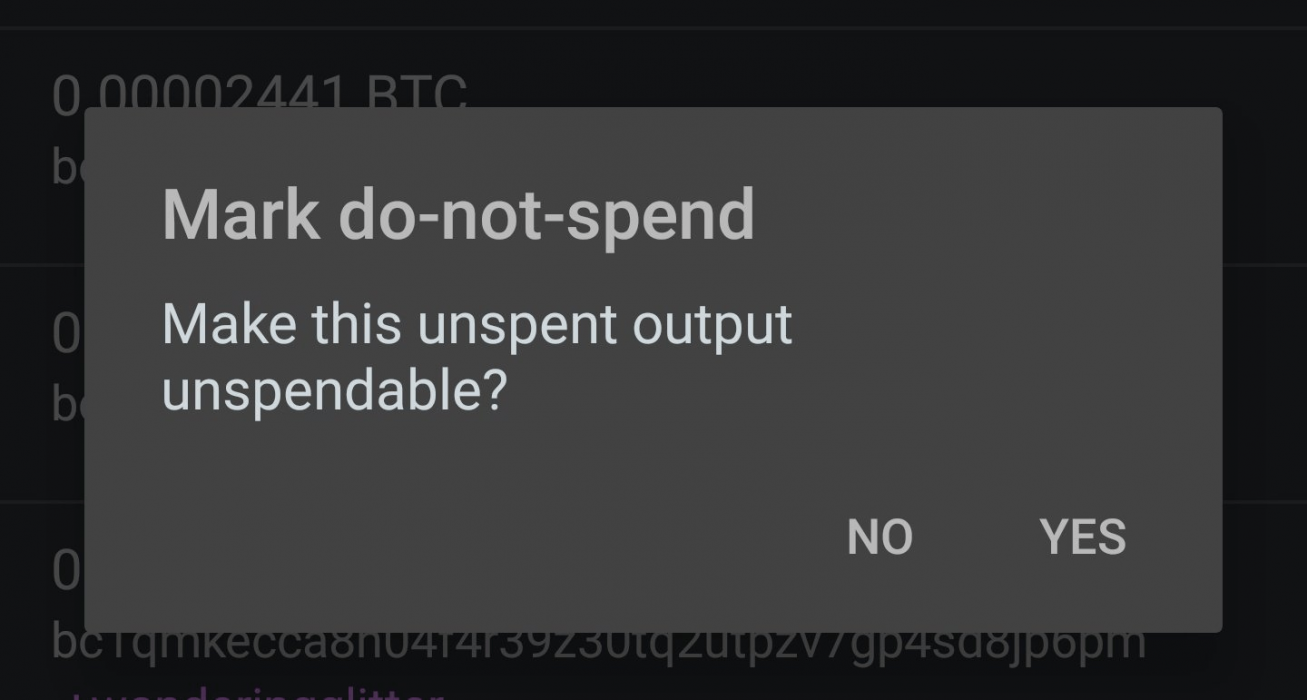
If you have been “dusted”, look for wallets that show dusty UTXOs (unspent transaction) and mark them as “do not spend” if your wallet or exchange allows you to do so. This will prevent them from being used for later transactions.
You can also use a hardware wallet to protect yourself as well – while expensive, they can be safer storage for your private keys.