There’s a new malware spreading across Europe and Australia – a virus targeting Android devices to harvest login credentials for online banking apps and crypto wallets in an automated way.
Vultur Wings Its Way to Australia
Vultur, a Remote Access Trojan (RAT) that was being tested in Italy and Spain, is now rapidly spreading across Australia. The virus has been installed over 5000 times via Google Play Store disguised as an app called “Protection Guard”, so the number of victims should be the same.
A RAT malware is smuggled into a device to control it remotely, relying on the function of Virtual Network Computing (VNC). Through VNC, hackers try to obtain personal information to carry out online fraud on a massive scale.
For the first time we are seeing an Android banking trojan that has screen recording and keylogging as the main strategy to harvest login credentials in an automated and scalable way.
ThreatFabric researchers
Detecting Vulture
Outside of recently downloading any apps with the name of “Protection Guard”, ThreatFabric suggested that there was a way to detect the RAT:
You can also detect Vulture because when it’s transmitting data to its command-and-control server, the active “casting” icon will show up in the Android notifications. If you’re not casting something and the icon shows up anyway, that’s reason to worry.
ThreatFabric
To reduce the risk posed by RATs such as Vulture, Android users would be advised to ensure that they have a reputable antivirus app running in the background to detect any potential threats when new apps are downloaded.
Buy a Hardware Wallet
The attackers are targeting major crypto exchanges and mobile wallets including Kraken, Coinbase, Binance, CEX, eToro and more. While Android devices are the main target, users believe the virus may soon reach iOS.
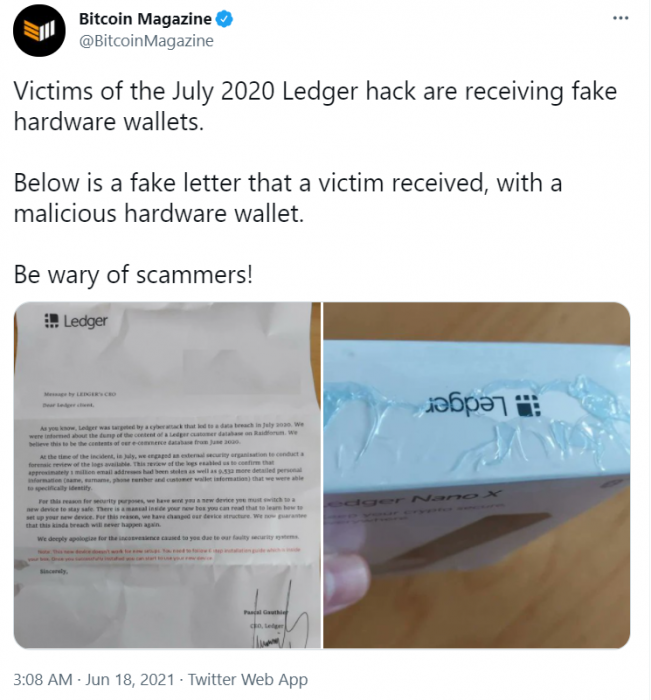
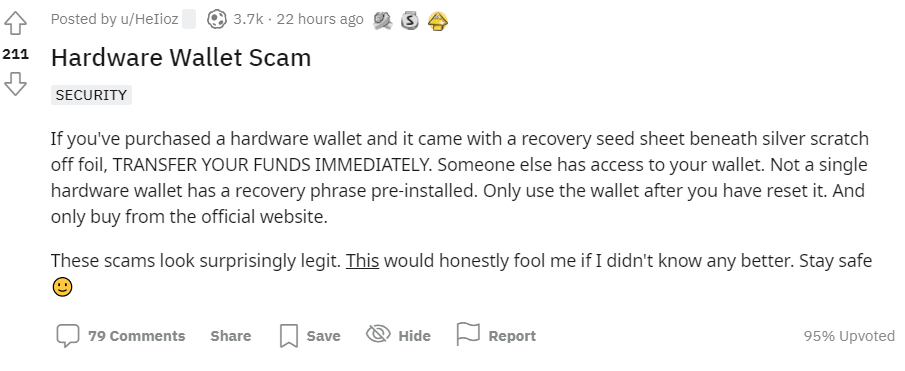
Crypto users are warning others on social media, recommending they do not store their funds on exchanges and, if possible, get a hardware wallet and save most of their funds on it.
Scams, Hacks and Glitches on the Rise
As hacks and crypto scams become more common, newcomers should be wary when choosing their wallets. Rather than leave their funds in a crypto exchange, they should store them in a hardware wallet.
Roll, for instance, was a decentralised finance protocol attacked in March by a group of hackers that drained its wallet of over US$5.7 million. To this day, developers still don’t know how the platform got hacked.
As always, you can keep up to date with the many and varied scams out there by consulting Crypto News‘ comprehensive guide.