DeFi protocol Ola Finance has called on users to resist pointing fingers of blame and asked the community instead to focus on the growth of the project, as it addressed a US$3.6 million hack via Twitter on April 1.
The attack took place on Fuse Lending, Ola’s implementation on the Fuse blockchain:
Re-Entrancy Bug Responsible for Theft
The incident involved a “re-entrancy bug”, which is a commonly known culprit at the heart of DeFi attacks. The smart contract vulnerability enables hackers to make repeated calls to a protocol in order to steal assets, without having to pay back borrowed funds.
The attack began by mixing funds through Tornado Cash, making the crypto hard to trace. The funds were then withdrawn over the Fuse Bridge and transferred to the Fuse network (Ola’s decentralised lending platform). The hacker used the assets as collateral to take out loans, and by exploiting the re-entrancy bug was able to then remove the starting funds without having to repay the loans.
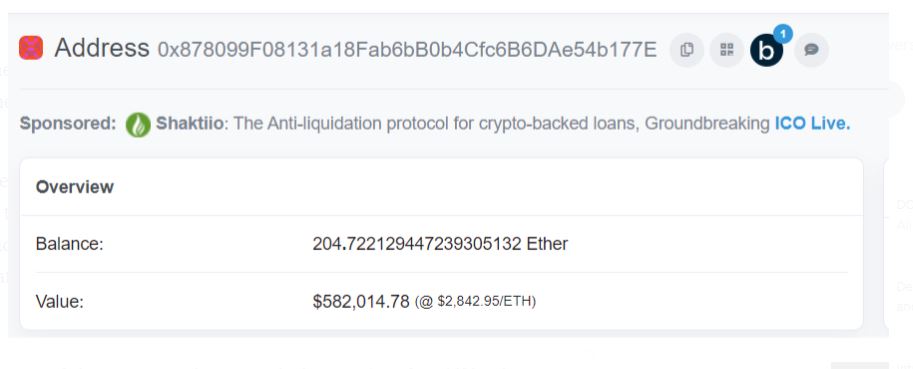
This process was repeated several times across different Ola pools. The hacker then transferred the drained assets to wallets on Ethereum and BNB Chain. In total, the hacker holds US$3 million on Ethereum and another US$637,000 on BNB Chain.
Official Report Forthcoming
Ola tweeted that it would soon publish an “official report detailing the exploit”. For now it has responsibly paused the use of the Fuse network lending protocol while looking into rectifying the bad code.
This is not the first, nor will it be the last, re-entrancy attack in DeFi. Only two weeks ago, Agave and Hundred Finance, two lending DeFi protocols, were exploited for approximately US$11 million. Three months ago, Grim Finance DeFi protocol was hacked for US$30 million in Fantom tokens as attackers exploited a flaw in the vault contract.