The US Justice Department has impounded US$3.6 billion in bitcoin and arrested a would-be rapper and her husband for conspiring to launder some of the funds – believed to be among the proceeds of the infamous Bitfinex hack of 2016.
According to the FBI, Heather Morgan and her husband Ilya Lichtenstein spent part of the proceeds on gold, NFTs, and other items. Each faces up to 25 years in a federal prison if convicted.
Rather than keep a low profile as you’d expect of alleged crypto criminals, Morgan in particular has a social media presence befitting her status as an aspiring rapper, published writer and influencer. She even has a website dedicated to her rapper alter-ego, named “Razzlekhan”:
Morgan’s LinkedIn profile notes her economics degree, while as a journalist the 31-year-old has been published in Inc and Forbes magazines, with the latter running an article of hers ironically titled “How to Protect Your Business From Cyber Criminals”.
How the FBI ‘Followed the Money’
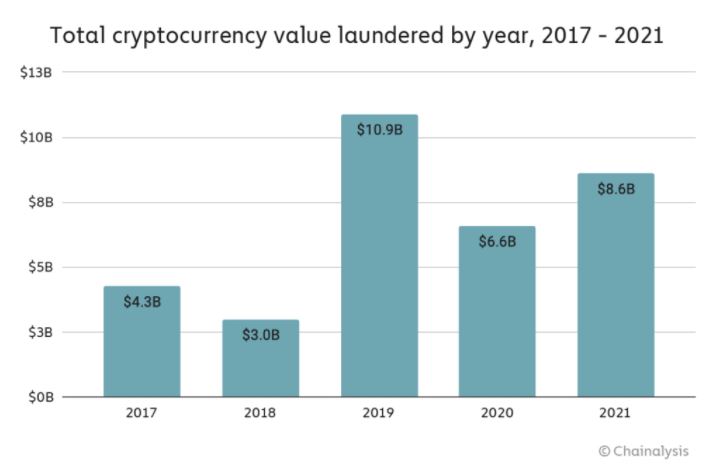
The Bitfinex hack involved the theft of 119,756 bitcoin (worth just US$72 million at the time) following a security breach at the exchange. The amount stolen is now valued at more than US$5.1 billion.
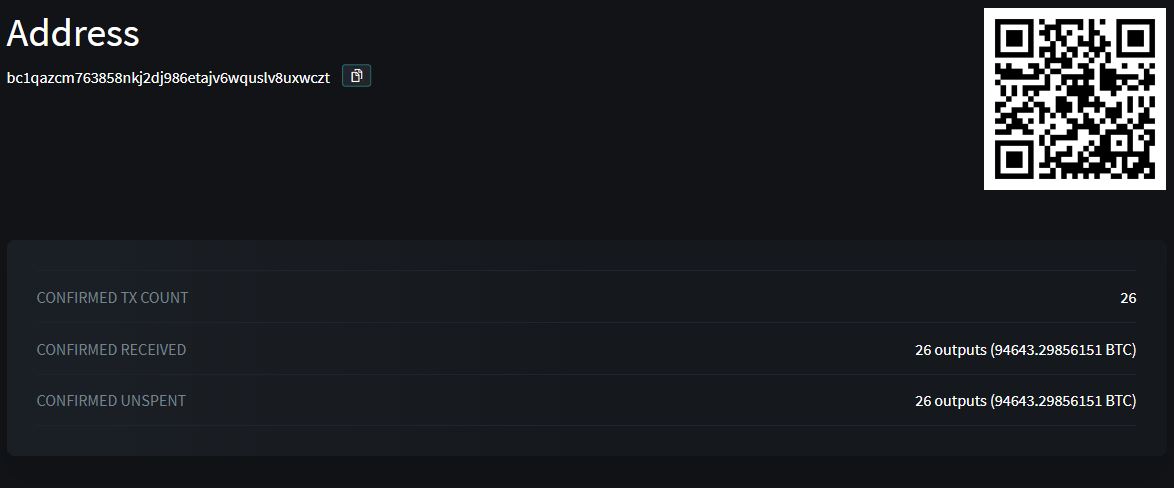
In the five years since the hack, small amounts of BTC have periodically been moved in separate transactions, leaving the bulk of the funds untouched. The Justice Department traced 25,000 BTC of these transferred funds to financial accounts controlled by Lichtenstein and Morgan. Special agents were then able to gain access to and seize more than 94,000 BTC – worth US$3.6 billion at the time – from Morgan and Lichtenstein after a search warrant allowed them to view files containing private keys to several wallets, which just days ago were consolidated into a single wallet.
Morgan and Lichtenstein allegedly used a variety of methods to launder the illicit crypto, including chain hopping, depositing the coins at exchanges and darknet markets and withdrawing them, and automating transactions using computer programs. In addition, the pair set up business accounts in the US to “legitimise their banking activity”.
“[These] arrests, and the department’s largest financial seizure ever, show that cryptocurrency is not a safe haven for criminals,” said US Deputy Attorney General Lisa Monaco.
“The [Justice] department once again showed how it can and will follow the money, no matter what form it takes.”
US Deputy Attorney General Lisa Monaco
The Justice Department must, of course, still prove its allegations in court that Morgan and Lichtenstein laundered the US$4.5 billion in bitcoin stolen from Bitfinex in 2016. The hack is a separate matter.