In a compelling display of how bitcoin is unsuitable for criminal activities, Netherlands-based Maastricht University has shared a positive tale of how the bitcoin it paid in ransom in 2019, since tracked and recovered, has appreciated significantly in the interim:
A Profitable Ransom
As outlined by the university, it suffered a ransomware attack in 2019 that prevented more than 25,000 staff and students from accessing critical research data, email, or library resources. The hackers encrypted hundreds of Windows servers and backup systems, denying access to business-critical services pending a ransom payment of €200,000 (US$208,000) in bitcoin.
As reported by Dutch newspaper De Volkskrant, the university agreed to pay the attackers after a week, “partly because personal data was in danger of being lost and students were unable to take an exam or work on their theses”.
After launching an investigation, Dutch police traced a Ukrainian bank account belonging to a known money launderer. Investigators were able to establish that a relatively small amount of the ransom money, some €40,000 (US$41,000) worth of bitcoin, had been paid.
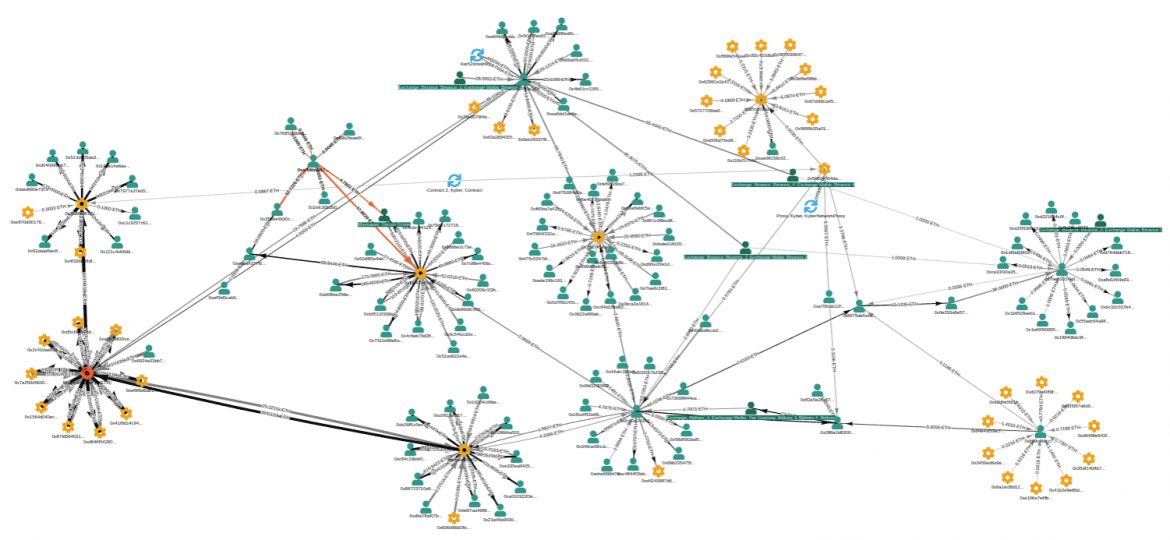
Prosecutors were able to seize the offending account in 2020 and, through chain analysis techniques, were able to trace the remaining bitcoin. While information remains limited on why it took so long to return the funds, it appears as if the tedious wheels of bureaucracy might have worked in the university’s favour.
Since paying the ransom, the €200,000 (US$205,000) worth of bitcoin has more than doubled to €500,000 (US$515,000), even despite bitcoin plummeting some 75 percent below its all-time high.
Needy Students to Benefit from Recovery
Commenting on the windfall, Maastricht University ICT director Michiel Borgers said it would be directed to students in need:
This money will not go to a general fund, but into a fund to help financially strapped students.
Michiel Borgers, director of ICT, Maastricht University
De Volkskrant has reported that the investigation remains ongoing as authorities search for those responsible for the exploit. As crypto crimes soared to new heights in 2021, efforts to combat ransomware attacks have been increasingly ramped up by authorities including the US Federal Bureau of Intelligence, which recently established its crypto crime unit.














