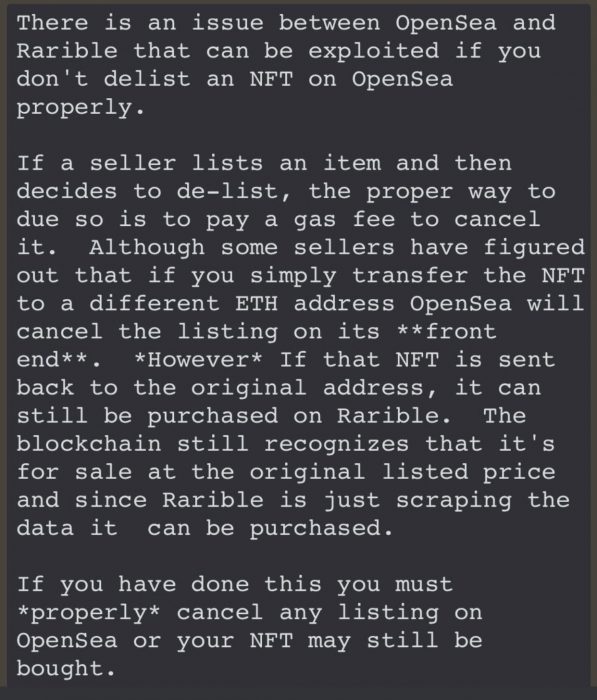
A bug has been exploited by hackers to purchase NFTs from OpenSea users at well below market value. The loophole allowed Bored Ape #8924 to be snatched up for an old sale price listing of only 6.66 ETH (about US$16,200), leaving its seller, VirtualToast.eth, very angry.
VirtualToast.eth expressed his outrage at OpenSea’s negligence and warned other users of the platform’s flaw, urging them to remove all permissions for OpenSea to avoid suffering the same fate:
The bug allows attackers to snap up NFTs at previously listed prices (chosen by the seller in the past), which are often well below current market prices. The exploit relies on the fact that NFT owners are unaware that old marketplace listings for their NFTs are still active. This is due to the seller not delisting the item correctly by paying a gas fee. The Messenger | NFT posted on Twitter to help explain the issue:
To protect users, Rarible was quick to temporarily disable all OpenSea orders on Rarible.com. It also developed a tool, Rarible Order Manager, to allow everyone to see and cancel their potentially risky sale orders.
Other NFTs Flipped Following Exploit
Etherscan has dubbed the account in question “OpenSea Opportunistic Buyer”. The exploit allowed the buyer in question (who goes by the name “jpegdegenlove“) to successfully purchase other NFTs at heavily discounted prices, including BAYC NFT #8274 for just under 23 ETH (around $56,000) and BAYC #9991 for just 0.77 ETH (about $1,800). The floor price for a BAYC NFT is currently 86 ETH, worth almost $210,000 at the time of writing.
“Jpegdegenlove” bought seven NFTs in the hack, paying a total of $133,000, before immediately flipping them for $934,000 in ETH and sending the funds through Tornado Cash.
Interestingly, “jpegdegenlove” seems to have partially compensated two of his/her victims, sending 20 ETH ($49,000) to “TBALLER” and 13 ETH ($32,000) to “Vault327”.
This isn’t the first time OpenSea has been criticised for flaws in its code. Just a few months ago, Crypto News Australia reported a bug on the platform that destroyed at least 42 NFTs worth around US$100,000.