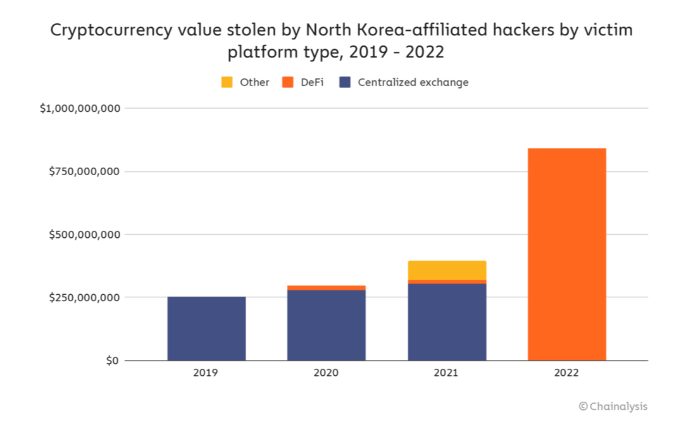
Blockchain analytics firm Chainalysis has published a new report about criminal activities in the cryptocurrency space, stating that 97 percent of crypto hacks have targeted DeFi projects since the beginning of 2020.
North Korean Hacking Groups Largely Responsible
According to the report, DeFi protocols accounted for 97 percent of the US$1.68 billion worth of cryptocurrency stolen. Most of the stolen funds, approximately US$840 million, have gone to hacking groups associated with the North Korean government, the report says.
On March 30, Axie Infinity lost over US$600 million in the biggest DeFi hack on record. The US government linked the heist to a notorious North Korean-based hacking group called Lazarus.
Another recent incident occurred on May 3 when a hacker stole US$80 million from DeFi platform Rari Capital.
DeFi-Based Money Laundering on the Rise
DeFi protocols have also seen an uptick of illicit funds coming into their networks. According to the report, 69 percent of all funds in DeFi were sent from addresses linked to criminal activity.
DeFi protocols allow users to trade one type of cryptocurrency for another, which can make it more complicated to track the movement of funds – but unlike centralised services, many DeFi protocols provide this ability without taking KYC information from users, making them more attractive to criminals.
Chainalysis report
Another key finding of the report was the incidence of NFT wash trading. This practice consist of artificially inflating the price of an asset by buying and selling the same instrument at the same time.
Chainalysis put up as an example two wallets that generated over 650,000 WETH in transaction volume by selling the same three NFTs back and forth to one another. The wash trade was done in the same marketplace, as it rewards transactions on its marketplace.